An American computer security firm that has traced a series of cyberattacks across the globe to the Chinese military says Asia may be more vulnerable than previously thought to Beijing's economic espionage operations, even as experts see the region beefing up its cybercapabilities.
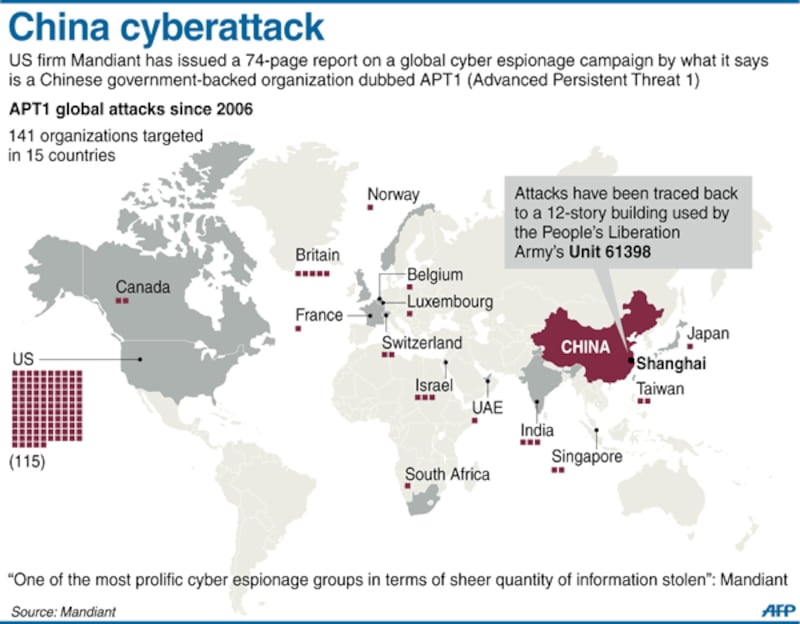
Mandiant Corp. last week published the extraordinary details of hacking attacks it believes were masterminded by a unit of the People's Liberation Army to steal commercial secrets from at least 141 entities worldwide, but mostly inside the U.S., over the last seven years.
Although it listed only eight Asian institutions among groups targeted by hackers shepherded by PLA's Shanghai-based Unit 61398, Mandiant believes the number of organizations in the region infiltrated by Chinese cybersnooping may be much higher.
The broader threat posed to Asia is reflected in the wide spectrum of industries in the region that were implicated in the cyberattacks scrutinized by Mandiant, according to experts at the Virginia-based firm.
In its global assault on 141 entities, the Chinese group, dubbed APT1, carried out corporate espionage across 20 major industries, the officials said.
In Asia, eight entities covering six industries fell prey to APT1’s attacks, said a senior official of the firm, which serves about 40 percent of the Fortune 500 companies but has no Asia presence.
"From the sample size of the eight compromised organizations inside Asia, it is pretty surprising that six different industries have been hit," Dan McWhorter, managing director of Mandiant's threat intelligence unit, told RFA.
"I think that having eight victims inside of Asia shows that there is probably a lot more going on," he said.
"We are primarily a U.S. company. We don't have fantastic visibility in Asia, so to see this many victims without us even working in that market could be cause for concern."
Detailed charges
Mandiant's in-depth report by intelligence analysts contains some of the most detailed charges against China's economic espionage operations, including a time line and details of the used malware—short for malicious software created by attackers to disrupt computer operations and gather sensitive information.
The report identified the Asian nations targeted by the Chinese attacks as U.S. allies Japan, Singapore, and Taiwan as well as India, but did not identify the victims of the cyberattacks or Mandiant's customers.
McWhorter said the Asian entitles comprised two information technology companies, an electronics company, two governments, an international "organization," and two companies linked to transportation, satellites, and telecommunications.
Beijing has flatly rejected the corporate espionage charges by Mandiant, which accused the PLA-controlled hacking group located in Shanghai's Pudong financial hub of having stolen "hundreds of terabytes of data from at least 141organizations across a diverse set of industries beginning as early as 2006."
Mandiant had cited some of its evidence, including Internet protocol addresses and the identities of several Chinese individuals it believes were behind some of the attacks. The hackers were tracked by Mandiant as they logged onto social networking sites or through e-mail accounts.
The cyberthreat report came as the United States outlined policies for wider sharing of government data on hacking with private companies and called for voluntary cybersecurity standards for those businesses.
In Asia, Chinese cyber espionage is posing "a serious and persistent challenge to regional security," Russell Hsiao, an expert at Virginia-based The Project 2049 Institute, told RFA.
For instance, he said, Taiwan is the first and most intense target of Beijing-sponsored cyber espionage.
In spite of the thaw in tensions between China and Taiwan over recent years, Taiwan’s intelligence chief Tsai Der-sheng stated in 2012 that Chinese hackers have been launching attacks on Taiwan-based websites, reportedly exfiltrating more than 26,000 data pieces over the past seven years, Hsiao said.
The Project 2049 Institute two years ago mapped out in great detail how different operational units and organizations under the PLA's powerful Third Department of the General Staff Department function within the Chinese military’s burgeoning cyber surveillance program, he said.
In its report, the U.S. group identified the 61398 unit and its auxiliary offices as likely having the lead on the targeting of United State and Canada.
'Strategic cyber competition'
Experts say the Mandiant report underscores the key roles of information technology and cyberspace in Chinese politics, strategy, and economic policy as competition intensifies among Asian economies and amid heightened strategic rivalry between the United States and China in the region.
"The concerns over strategic cyber competition may be global, but it is Asia with its political tensions, vigorous economies, and lack of strong multilateral institutions that is a focal point for this new form of competition," said James Lewis, Director of the Technology and Public Policy Program at the Washington-based Center for Strategic and International Studies.
"And it is the rise of China and its extensive cyber capabilities that defines strategic competition in both Asia and cyberspace globally," he said in a blog of Australia's Lowy Institute for International Policy.
Lewis said Chinese government agencies, companies, and individuals have expanded their efforts in cyberspace to illicitly acquire technology or gain business advantage. He drew parallels between Beijing's five-year economic plans and cyber espionage activities that appear to have originated in China.
For instance, he said, China has long sought the means to develop an indigenous computer central processing unit (CPU), and Intel Corporation, the world's leading producer of CPUs, was a target of a January 2010 corporate hacking which also involved Google.
"The most damaging aspect of cyber spying is economic espionage, where technology, research products, confidential business information, and intellectual property can all be stolen. The damage may not be visible immediately in an economy, but then the goal of espionage is not to be detected," Lewis said.
Amid the increasing threat from China, Asian economies are boosting their cyber defenses.
Lewis said the United States, China, and Russia have the most advanced cyber capabilities in Asia.
"The capabilities of other Asian nations range from nominal to relatively sophisticated, albeit not in the top tier," he said.
Judging from public sources, he said, 10 Asian nations are developing cyber capabilities.
Seven are developing military capabilities and doctrine: Australia, China, North Korea, India, Malaysia, Burma, and South Korea while another three—Brunei, Japan, and Singapore—are developing defense-only capabilities, Lewis said.
The United States meanwhile is being asked to establish a cyber alliance with Asian allies to thwart the Chinese cyberthreat.
"The United States should set up a center for cyberdefense that would bring together the best minds from allied countries to develop countermeasures and conduct offensive activities," said Dan Blumenthal, the director of Asian studies at the Washington-based American Enterprise Institute.
He said in a commentary in the Foreign Policy journal that one such center could be Taiwan, "as its understanding of Chinese language, culture, business networks, and political landscape make it invaluable in the fight against cyberattacks."
"Of course, centers could be placed elsewhere and still utilize Taiwan's knowledge, but even the threat of placing a cyberdefense center just across the strait would be very embarrassing for China's leaders, as Taiwan is viewed as a renegade province."
"The point is not to be gratuitously provocative, but rather to demonstrate that the United States [has] options that China would not favor."
Revising laws
Adam Segal, an expert at the New York-based Council on Foreign Relations said key U.S. ally Japan's ruling Liberal Democratic Party is well placed to “reinforce cybersecurity as national security” in Japan, which is the second biggest economy after China.
"Revising the war contingency bill [in Japan] to include cyberattacks and enacting a law to protect classified information should make it easier for Tokyo to cooperate with Washington," he said.
Another U.S. ally, South Korea, recently signed a deal for the joint development of a “Global Cybersecurity Center,” while India has announced a five-year plan to reform the country’s cybersecurity institutions as well as boost new cooperation with Britain and expanded dialogue with Japan on cybersecurity, he noted.
The United States and Australia have also declared that their mutual defense treaty applies to cyberattacks, with Canberra recently announcing the establishment of the Australian Cyber Security Centre.
As U.S. President Barack Obama looks toward Asia in his second term, Chinese cyber espionage will be a "grain of sand in the eye" and "is not going away any time soon," Segal said, adding that there are steps Obama can take "to make it slightly less annoying."
"Moreover, many of the policies to mitigate the situation will overlap with other efforts to re-energize the U.S. presence and boost ties to allies and friends in the region," he said.
